 Fox RAT V 6.0
Fox RAT V 6.0Fox RAT v6.0: Android-Based Remote Access
Fox RAT v6.0 is a sophisticated Android malware designed for unauthorized remote surveillance and control of infected devices. It grants attackers extensive access to sensitive data and system functions, enabling persistent monitoring and manipulation. Key feature categories include:
- Reconnaissance and Data Extraction Fox RAT V 6.0:
- Phone Information (device specs, IMEI, etc.)
- File Management (browse, upload/download files)
- Call Record and SMS Record (logs of communications)
- Contact Person (full address book access)
- Phone Account (credentials and login details)
- Application Information (installed apps and usage data)
- Personal Information (user profiles, location, etc.)
- Real-Time Surveillance Fox RAT V 6.0:
- Mobile Phone Control (lock, wipe, or reboot)
- Screen Control (live streaming and interaction)
- Camera Surveillance (front/back camera access)
- Voice Monitoring (microphone recording)
- Keylogging (capture keystrokes for passwords/inputs)
- Phone Notification (intercept and read alerts)
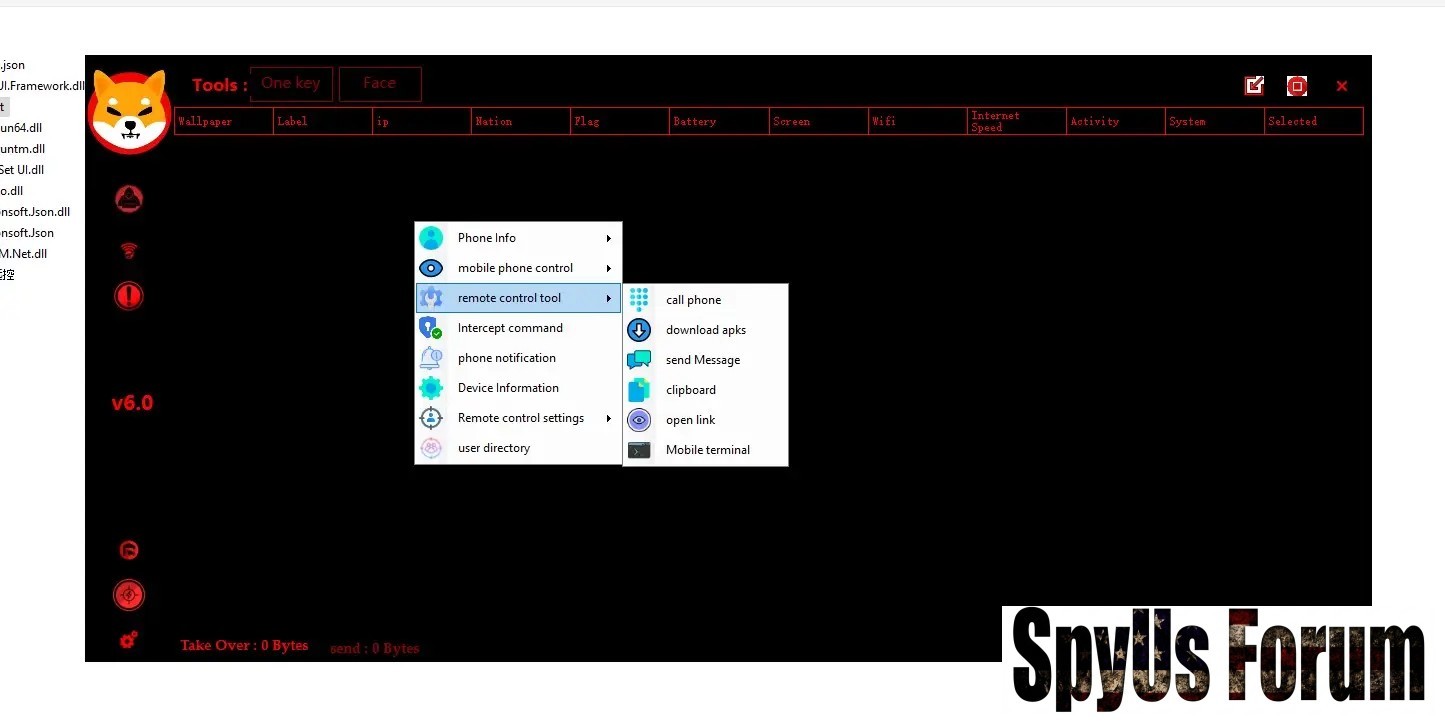
- Remote Exploitation and Commands Fox RAT V 6.0:
- Call Phone (initiate outbound calls)
- Download APKs (install malicious apps silently)
- Send Message (SMS or app-based messaging)
- Clipboard (steal copied text)
- Open Link (launch URLs for phishing/drive-by attacks)
- Intercept Command (override user inputs)
- Remote Control Setting (configure persistence and stealth)
- User Directory (access app data and storage)
- Mobile Terminal (execute shell commands)
- Device Information (detailed hardware/software inventory)
Download Links:
Download Link 1:
You must be registered for see links
Download Link 2:
You must be registered for see links
Download Link 3:
You must be registered for see links


