 Doofi Stealer 2025
Doofi Stealer 2025What is Doofi Stealer 2025?
Unlike generic stealers that falter against updated protections, Doofi Stealer 2025 excels in decrypting Chrome’s V20 passwords—a critical feature for ethical hacking simulations or forensic analysis. It’s not just a tool; it’s a comprehensive suite for system reconnaissance, making it ideal for cybersecurity professionals testing defenses in controlled environments.
Key highlights:
- Open-Source Accessibility: Freely available on GitHub for community contributions.
- Python-Powered: Leverages Python 3.10+ for cross-platform compatibility (Windows-focused testing).
- FUD cr¥pt3r Integration: Ensures payloads evade detection in 2025’s threat landscape.
Core Features of Doofi Stealer 2025
Doofi Stealer 2025 packs a punch with features tailored for efficiency and stealth. Here’s a breakdown of its standout capabilities:
1. Advanced Data Extraction
- Chrome V20 Password Decryption: Seamlessly cracks and exports the latest Chrome browser passwords, autofills, and cookies—vital for simulating phishing or credential theft scenarios.
- Autofill and Wallet Stealing: New in V2.2, it harvests browser autofill data and scans for cryptocurrency wallets (e.g., MetaMask, Exodus) and traditional ones like PayPal.
- System Intelligence Gathering: Captures computer name (cname), public IP address, and user details for comprehensive profiling.
- FUD cr¥pt3r: Built-in obfuscation to make compiled executables undetectable by AV tools like Windows Defender or third-party scanners.
- Admin Privileges and Startup Execution: Forces elevated runs and auto-starts with Windows for persistent access.
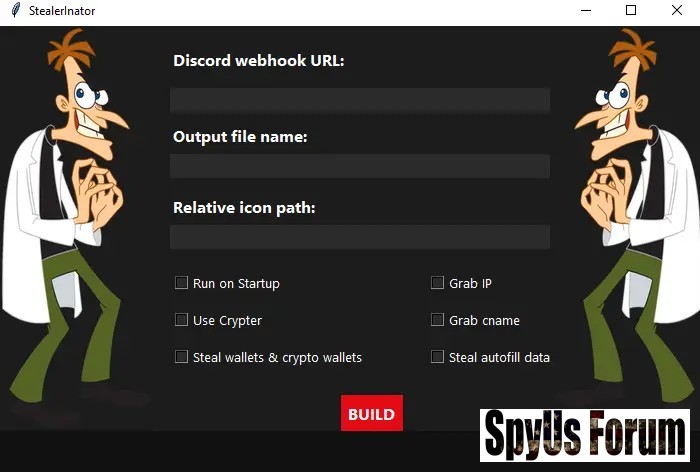
- GUI Overhaul (V2.1+): Intuitive graphical interface for selecting modules, inputting webhooks, and customizing output files.
- Modular Options: Toggle features like password stealing or wallet extraction to build lightweight, targeted payloads.
- One-Click Build: Generates standalone .exe files ready for deployment.
Getting started with Doofi Stealer 2025 is straightforward, ensuring minimal barriers for developers and testers. Here’s what you need:
Minimum Requirements
- Python Version: 3.10 or higher (tested on 3.10 for optimal performance).
- Operating System: Windows 10/11 (primary focus; adaptable for others with tweaks).
- Dependencies: Handled via a simple setup script—no manual pip installs required.
- Download the Repository: Head to the GitHub releases page and grab the latest ZIP or clone via Git:
- Build Your Payload: Launch the GUI, select desired features (e.g., enable Chrome V20 decrypt and wallet steal), choose output format (.exe or .py), and hit “BUILD.” The FUD cr¥pt3r kicks in automatically for AV evasion.
How to Use Doofi Stealer 2025: A Practical Guide
Once built, deploying Doofi Stealer 2025 is as simple as social engineering a target or integrating into a pentest toolkit. Here’s a quick usage workflow:
- Customization in GUI:
- Toggle modules: Enable “Run as Admin” for pr!v!l3g3 3sc@l@t!0n and “Startup Persistence” for longevity.
- Output Options: Specify file naming (e.g., victim_logs_2025.zip) for organized exfiltration.
- Deployment:
- Distribute the .exe via email, USB, or drive-by downloads in simulated attacks.
- Upon execution, it silently gathers data: passwords, IPs, wallets, and more.
- Monitoring Logs:
- Example log snippet:
{ "cname": "VictimPC-2025", "ip": "192.168.1.100", "passwords": ["site:example.com | user:admin | pass:Secret2025"] }
- Advanced Tips:
- Integrate with obfuscators like PyArmor for extra FUD layers.
- Test in a VM to validate V20 Chrome compatibility before live runs.
For ethical hackers, it’s invaluable for awareness training; for researchers, it’s a sandbox-ready prototype. GitHub’s active repo ensures ongoing updates, with no published packages yet hinting at untapped potential for forks.
Pros:
- Lightning-fast builds and extractions.
- 100% Python—easy to audit and modify.
- Free and community-driven.
- Windows-centric (Linux/Mac tweaks needed).
- Requires basic Python knowledge for customizations.
Ready to build? Fork the repo and join the conversation. For more on “advanced Python stealers 2025,” subscribe to our newsletter or explore related GitHub gems.
Disclaimer: This article is for educational and ethical research purposes only. Misuse of stealers constitutes illegal activity. Always obtain permission for testing.
Download Links:
Download Link 1:
You must be registered for see links
Download Link 2:
You must be registered for see links
Download Link 3:
You must be registered for see links


