 Version: V 3.1
Version: V 3.1Size: 30 MB
Date: April 13, 2025
PASSWORDSPRO V3.1 with ALL PLUGINS
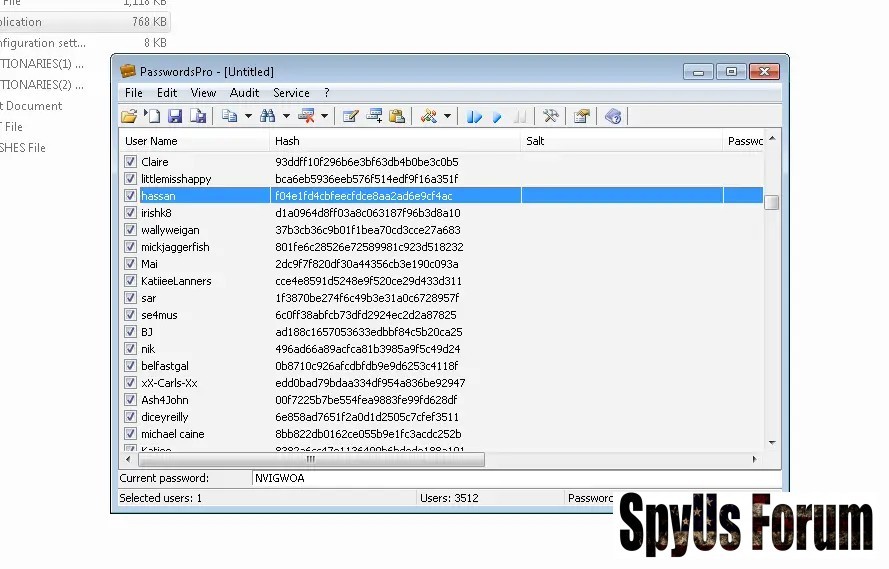
 Preliminary Attack – this is a quick check of user hashes for matching to simple passwords like “123”, “qwerty”, “99999”, etc., as well as to passwords found by the program earlier.
Preliminary Attack – this is a quick check of user hashes for matching to simple passwords like “123”, “qwerty”, “99999”, etc., as well as to passwords found by the program earlier.Brute Force Attack – this is the exhaustive search through all possible passwords in a certain range; e.g., “aaaaaa”…”zzzzzz”. Mask Attack – this attack is used when some information on the lost password is known. To use the attack, make sure to specify the mask for each character in the password to be recovered in the attack settings. For mask characters you can use the conventional characters for the standard or custom character sets – ?u, ?d, ?2, etc. (see the “Character Sets” tab in the program’s settings). Simple Dictionary Attack – during this attack, the program simply checks hashes against passwords in dictionaries. Combined Dictionary Attack – during this attack, passwords are made of several words taken from different dictionaries. That allows to recover complex passwords like “superadmin”, “admin*admin”, etc. Hybrid Dictionary Attack – this attack allows modifying passwords taken from dictionaries (for example, shift the password to upper case, append ‘1’ to the end of the password, etc.) and validating them as user passwords. The actions performed over source passwords are called “rules”, and the full list of those is available in the file “Rules.txt” in the distributive. Rainbow Attack – this attack attempts to recover passwords using the pre-calculated Rainbow tables.
- Adler-32
- Blowfish(Eggdrop)
- Blowfish(OpenBSD)
- CRC-16
- CRC-16-CCITT
- CRC-32
- CRC-32(ZIP_Seed)
- CRC-32B
- CRC-64
- DCC2
- DES(Oracle)
- DES(Unix)
- Domain Cached Credentials
- ELF-32
- FCS-16
- FCS-32
- Fletcher-32
- FNV-32
- GHash-32-3
- GHash-32-5
- GOST R 34.11-94
- HAS-160
- Haval-128
- Haval-128(HMAC)
- Haval-160
- Haval-160(HMAC)
- Haval-192
- Haval-192(HMAC)
- Haval-224
- Haval-224(HMAC)
- Haval-256
- Haval-256(HMAC)
- Lineage II C4
- MD2
- MD2(HMAC)
- MD4
- MD4(HMAC)
- MD5
- md5($pass.$salt)
- md5($pass.$salt.$pass)
- md5($pass.md5($pass))
- md5($salt.’-‘.md5($pass))
- md5($salt.$pass)
- md5($salt.$pass.$salt)
- md5($salt.$pass.$username)
- md5($salt.md5($pass))
- md5($salt.md5($pass).$salt)
- md5($salt.MD5($pass).$username)
- md5($salt.md5($pass.$salt))
- md5($salt.md5($salt.$pass))
- md5($salt.md5(md5($pass).$salt))
- md5($username.0.$pass)
- md5($username.LF.$pass)
- md5($username.md5($pass).$salt)
- md5(3 x strtoupper(md5($pass)))
- MD5(APR)
- MD5(Cisco PIX)
- MD5(Custom)
- MD5(HMAC(WordPress))
- MD5(HMAC)
- md5(md5($pass))
- md5(md5($pass).$pass)
- md5(md5($pass).$salt)
- md5(md5($pass).md5($pass))
- md5(md5($pass).md5($salt))
- md5(md5($salt).$pass)
- md5(md5($salt).md5($pass))
- md5(md5($username.$pass).$salt)
- md5(md5(md5($pass)))
- md5(md5(md5(md5($pass))))
- md5(md5(md5(md5(md5($pass)))))
- MD5(phpBB3)
- md5(sha1($pass))
- md5(sha1(md5($pass)))
- md5(sha1(md5($pass)).sha1($pass))
- md5(sha1(md5(sha1($pass))))
- md5(strrev($pass))
- md5(strtoupper(md5($pass)))
- MD5(Unix)
- MD5(WordPress)
- MSSQL(2000)
- MSSQL(2005)
- MySQL
- MySQL5
- NTLM
- Palshop
- RAdmin v2.x
- RipeMD-128
- RipeMD-128(HMAC)
- RipeMD-160
- RipeMD-160(HMAC)
- RipeMD-256
- RipeMD-256(HMAC)
- RipeMD-320
- RipeMD-320(HMAC)
- SAPB
- SAPG
- SHA-1
- SHA-1(Django)
- SHA-1(HMAC)
- SHA-1(MaNGOS)
- SHA-1(MaNGOS2)
- SHA-1(Oracle)
- SHA-224
- SHA-224(HMAC)
- SHA-256
- SHA-256(Django)
- SHA-256(HMAC)
- SHA-256(PasswordSafe)
- SHA-256(Unix)
- SHA-384
- SHA-384(Django)
- SHA-384(HMAC)
- SHA-512
- SHA-512(Drupal)
- SHA-512(HMAC)
- SHA-512(Unix)
- sha1($pass.$salt)
- sha1($salt.$pass)
- sha1($salt.$username.$pass.$salt)
- sha1($salt.md5($pass))
- sha1($salt.md5($pass).$salt)
- sha1($salt.sha1($pass))
- sha1($salt.sha1($salt.sha1($pass)))
- sha1($username.$pass)
- sha1($username.$pass.$salt)
- sha1(md5($pass))
- sha1(md5($pass).$salt)
- sha1(md5($pass).$userdate.$salt)
- sha1(md5(sha1($pass)))
- sha1(md5(sha1(md5($pass))))
- sha1(sha1($pass))
- sha1(sha1($pass).$salt)
- sha1(sha1($pass).substr($pass,0,3))
- sha1(sha1($salt.$pass))
- sha1(sha1(sha1($pass)))
- sha1(strtolower($username).$pass)
- sha256($pass.$salt)
- sha256($salt.$pass)
- sha256(md5($pass))
- sha256(sha1($pass))
- sha384($pass.$salt)
- sha384($salt.$pass)
- sha512($pass.$salt)
- sha512($salt.$pass)
- Skein-1024
- Skein-1024(384)
- Skein-1024(512)
- Skein-256
- Skein-256(128)
- Skein-256(160)
- Skein-256(224)
- Skein-512
- Skein-512(128)
- Skein-512(160)
- Skein-512(224)
- Skein-512(256)
- Skein-512(384)
- Snefru-128
- Snefru-128(HMAC)
- Snefru-256
- Snefru-256(HMAC)
- SSHA-1
- strrev(md5($pass))
- strrev(md5(strrev(md5($pass))))
- substr(md5($pass),16,16)
- substr(md5($pass),8,16)
- Tiger-128
- Tiger-128(HMAC)
- Tiger-160
- Tiger-160(HMAC)
- Tiger-192
- Tiger-192(HMAC)
- Ventrilo
- Whirlpool
- Whirlpool(Double)
- Whirlpool(HMAC)
- WPA-PSK PMK
- XOR-32
- xsha1(strtolower($pass))
You must be registered for see links
Download Links:
[HIDE]
[/HIDE]



