404 cr¥pt3r Cracked
Cybercriminals rely heavily on crypters, which prevent from detecting harmful code and allow for the stealthy deployment of malware. Lazar cr¥pt3r, Janadark cr¥pt3r, CypherX cr¥pt3r, Orway cr¥pt3r, and Dark Comet cr¥pt3r are just a few of the many crypters out there. They all have their own special characteristics and capabilities that help them avoid detection and have the most possible impact from cyberattacks.
Cryptomers, at their most basic, are tools for obfuscating and encrypting harmful payloads so that they cannot be detected by conventional . As part of this procedure, the malware’s original code, which is called “plain text,” is converted into a garbled form, called “ciphertext.” Malware can bypass security measures and execute its destructive payload unimpeded since the ciphertext is designed to evade signature-based detection methods used by antivirus products.404 cr¥pt3r Cracked
A cr¥pt3r’s efficacy is measured in part by how well it achieves Full Undetectability (FUD), which means that cannot detect the encrypted malware in any way. Cybercriminals frequently aim to achieve FUD status as a key target when they want to maximize the impact and duration of their virus campaigns. In order to remain undetected for an extended period of time, FUD crypters use complex encryption methods and evasion strategies, such cr¥pt3r Token or Ageis cr¥pt3r.404 cr¥pt3r Cracked
Data theft, espionage, and financial fraud are only a few examples of the many harmful behaviors made possible by crypters, which is why their importance in contemporary cybercrime is immeasurable. Cybercrime is becoming more widespread and severe due to the availability of free internet crypters and cracked versions like CypherX cr¥pt3r Cracked, which further reduces the barrier to entry for would-be cybercriminals.404 cr¥pt3r Cracked
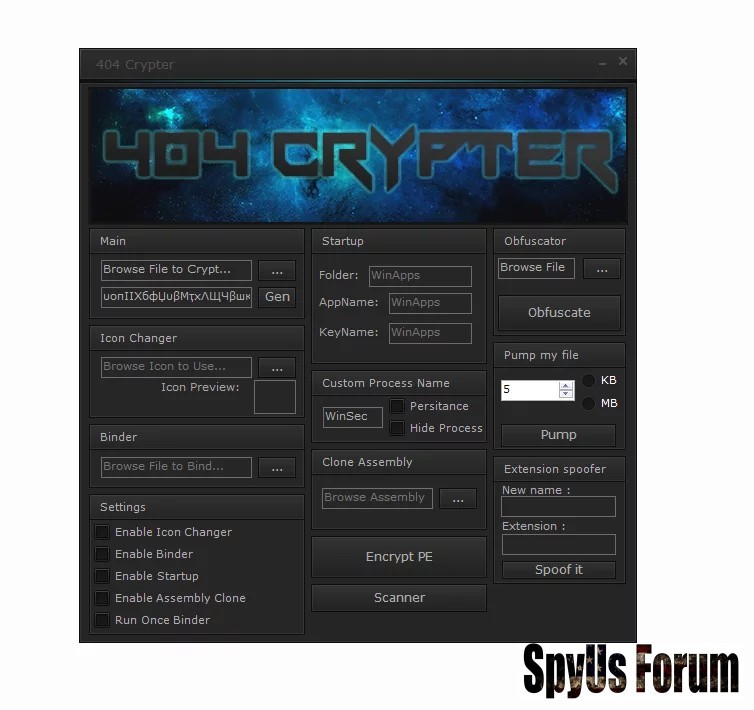
ICON Changer
Encryption
Start up
Obuscator
Custom Process Name
Size Pump
Extension Spoffer
Builtin Scanner
Binder
Start up
Assembly Changer
You must be registered for see links
Download Links:
Download Link 1:
You must be registered for see links
Download Link 2:
You must be registered for see links
Download Link 3:
You must be registered for see links